Modern servers are equipped with management processors enabling the remote administration and monitoring of all crucial system parameters. Most of them are based on the Intelligent Platform Management Interface (IPMI). But what does this term actually mean? Let’s have a look.
IPMI is a powerful protocol that is supported by multiple server devices from major manufacturers such as Dell, HP, Oracle and Lenovo. The IPMI specification itself has been developed by Intel, to allow administrators to manage their computer systems when you have no possibility to do that on the spot, through physical access. Working on the basis of the Baseboard Management Controller (BMC), the IPMI protocol is very practical. Not only does it provide access to the BIOS, disks and other hardware, but also supports multiple communication protocols, and operates independently of the operating system currently installed on the computer as well.
Risks stemming from the use of IPMI protocol
Judging by this short introduction alone you might think that IPMI is something of a technological revelation. But not entirely. Unfortunately, motherboards with IPMI functionality used with older versions of the IPMI firmware are affected by many security gaps, making them easy to identify and hack if only connected to the Internet.
Here are some of the major drawbacks of the IPMI protocol:
- Passwords for IPMI authentication are saved in plain text
- By knowing just one IPMI password it is possible to access all computers belonging to the IPMI managed group
- Main access to the IPMI system provides full control over both hardware and software
- The Baseboard Management Controller often uses excessive and legacy network services that may be particularly vulnerable to attacks
- IPMI can also provide remote console access to the system, and therefore, the BIOS
- Some types of BMC connections are not encrypted
Providing extra security
The above outline of biggest risks resulting from the use of IPMI protocol leaves no doubts why it is so crucial to establish additional safety measures for your data center. Let’s move then to the practical approach to this problem. Here are some of the most commonly implemented solutions:
- Limiting IPMI IP addresses to internal networks. IPMI traffic (usually UDP port 623) should be restricted to trusted internal networks, preferably to VLAN management segment only. If using IPMI outside the trusted network, scan and monitor it closely for any invalid activity.
- Using strong passwords. Devices operating within the IPMI system should have strong, unique passwords defined for the IPMI service.
- Encrypting traffic. If possible, enable the encryption option on IPMI interfaces. Detailed information on how to configure an encryption can be usually found in the manufacturer’s instruction manual.
- Authentication requirements. The “Cipher 0” function is an option enabled by default on many devices with active IPMI interface, allowing to ignore the authentication requirement. Disable this as well as the “Anonymous login” function to prevent hackers from bypassing authentication and sending any IPMI commands.
IPMI Proxy Server
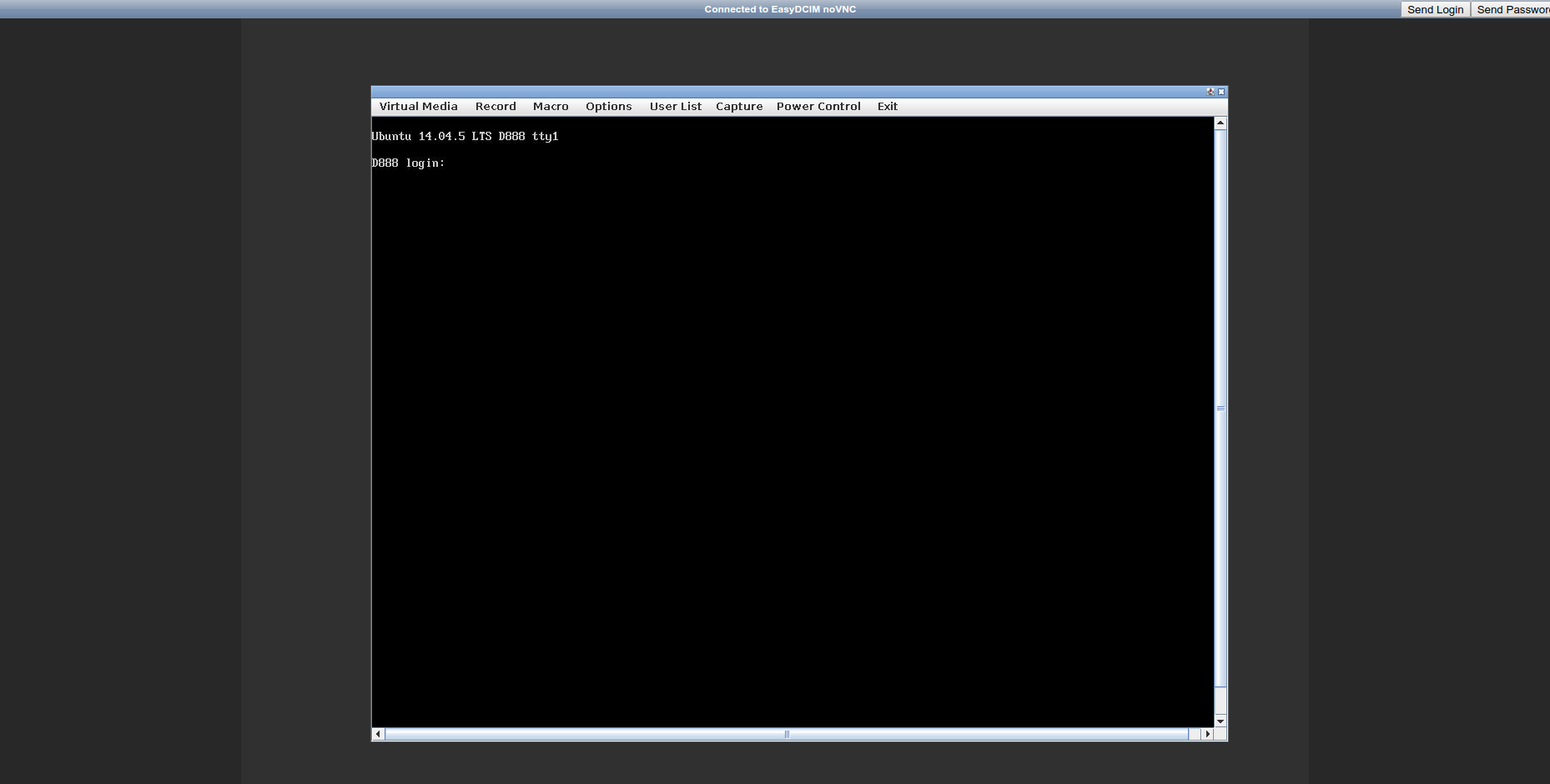
After configuring and securing your servers with IPMI support, you will definitely want to provide end users with access to the KVM console or default management panel. The latter contains plenty of details particularly useful from the customer’s point of view – system logs, information about the installed software and the properties of individual hardware components. Access to the KVM console, in turn, enables the remote access to the BIOS or SSH session.
IPMI Proxy Server requirements
The 1.5.2 version of EasyDCIM introduces the possibility to configure IPMI proxy server, and by doing so greatly improve the security layer of your infrastructure. To use the proxy server you need an additional server with the Debian 9 “Stretch” or Ubuntu 18.04 LTS (Bionic Beaver) system. Also, the server should have access to the internal network in which the IPMI IP is located. We recommend installing the proxy software on a separate server (either virtual or dedicated). The proxy server can have both a public and private IP address, but it must be available from EasyDCIM. It is possible to configure proxy on the EasyDCIM server, but we advise against it since every time you are using a proxy server with third-party software installed, the risk of unauthorized access to the target server significantly rises. Finally, please keep in mind that proxy increases the load on the proxy server, consequently slowing down the application.
Principle of operation
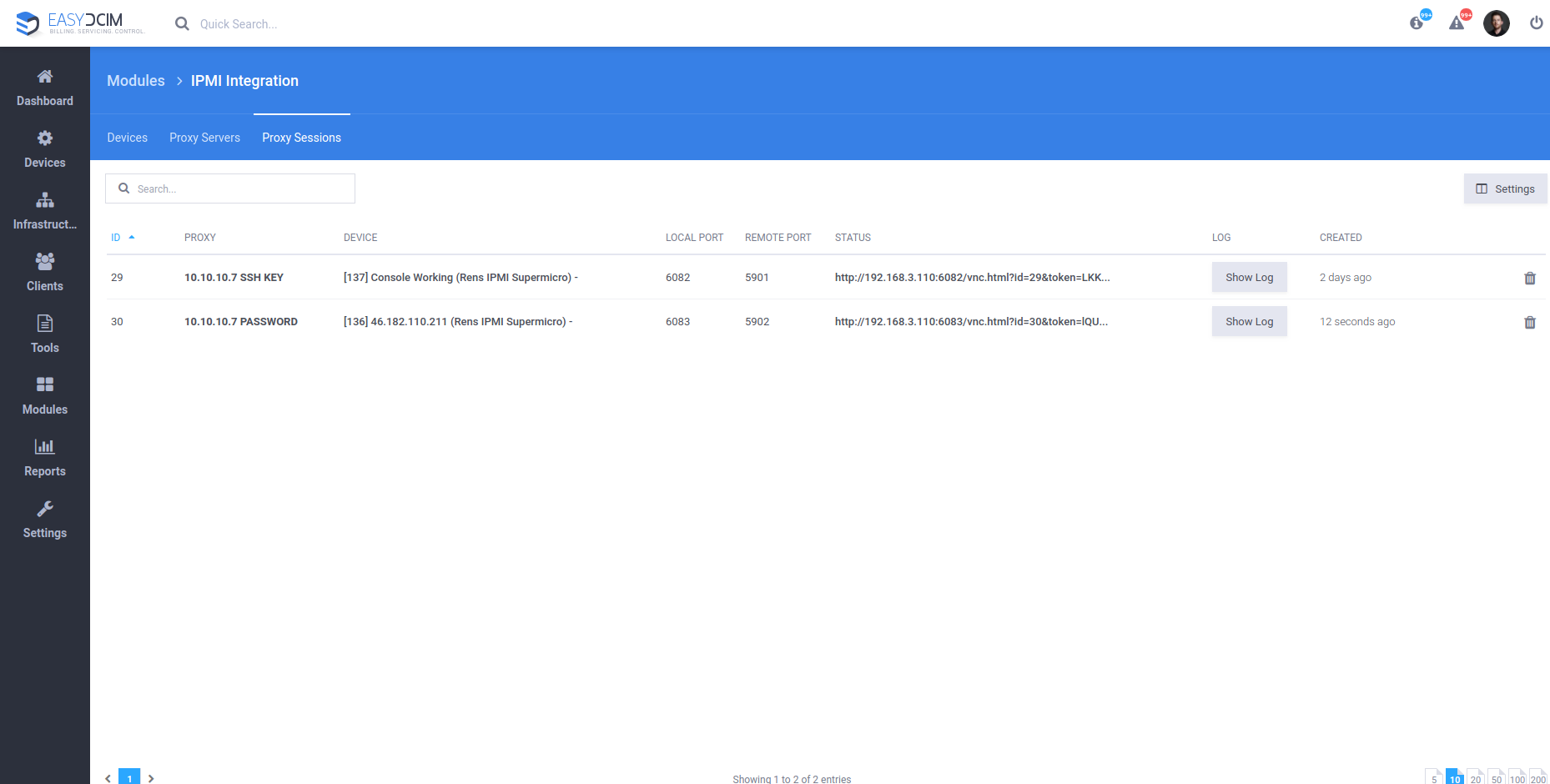
The remote JAVA console is downloaded directly from the server manufacturer’s panel, using the specific CURL commands. Additionally, to download the JAVA console, you need a public address of the IPMI interface which may lead to unauthorized access. If such a situation occurs, you can create a proxy server for IPMI connections in the application that will serve as a gateway between the application and the end user. The proxy server also channels all IPMI commands such as device power-on, restart or power-off. Owing to such a solution, none of the IPMI interfaces requires a public IP address and all important operations can be carried out in a secure private data center network.
Using a proxy server in EasyDCIM
EasyDCIM automatically creates a VNC session on the proxy server and launches the JAVA applet or the default management panel of the device. As a result, all devices are accessible only from the proxy server and all the traffic is transferred using a special image transfer system from the virtual graphic environment. Even though the VNC session runs in a secure manner, it is important to ensure that the proxy server is properly protected against any unauthorized access.
Conclusions
The vulnerabilities of IPMI-enabled systems are many and range from the ability to steal system password to the bypass of authentication mechanisms. Luckily, EasyDCIM v1.5.2 empowers data center administrators to mitigate the risk of authorized access attempts by configuring their own IPMI proxy servers that will redirect IPMI and KVM console commands.
Hope you enjoyed the article and learned a few new things about the double-edged sword nature of the IPMI protocol. If you are eager to soar the safety standards of your company even higher, stay tuned for our next Blog dedicated to ACL (Access Control List). And if you have not explored the 1.5.2 release in full yet, our latest post will brief you in on all new features now available!