IPMI Proxy
The extension enables the proxy connection between the EasyDCIM platform main server and the private IPMI network. It is one of the remote agent components and can only work with this remote agent. Here are the functions supported by the component:
- running the boot/reboot/shutdown actions directly on the remote agent server using the ipmitool command,
- downloading a JAVA KVM applet directly to the remote agent server from the IPMI manufacturer’s factory panel using appropriate CURL commands,
- starting a noVNC session along with a running JAVA KVM applet or the manufacturer’s factory panel.
Requirements
The remote agent server should have access to the internal network in which the IPMI IP is located. The proxy server can have both a public and private IP address, but it must be available from EasyDCIM control panel. It is possible to configure proxy on the EasyDCIM server (local agent), but we advise against it since every time you are using a proxy server with third-party software installed, the risk of unauthorized access to the target server significantly rises. Finally, please keep in mind that proxy increases the load on the proxy server, consequently slowing down the application.
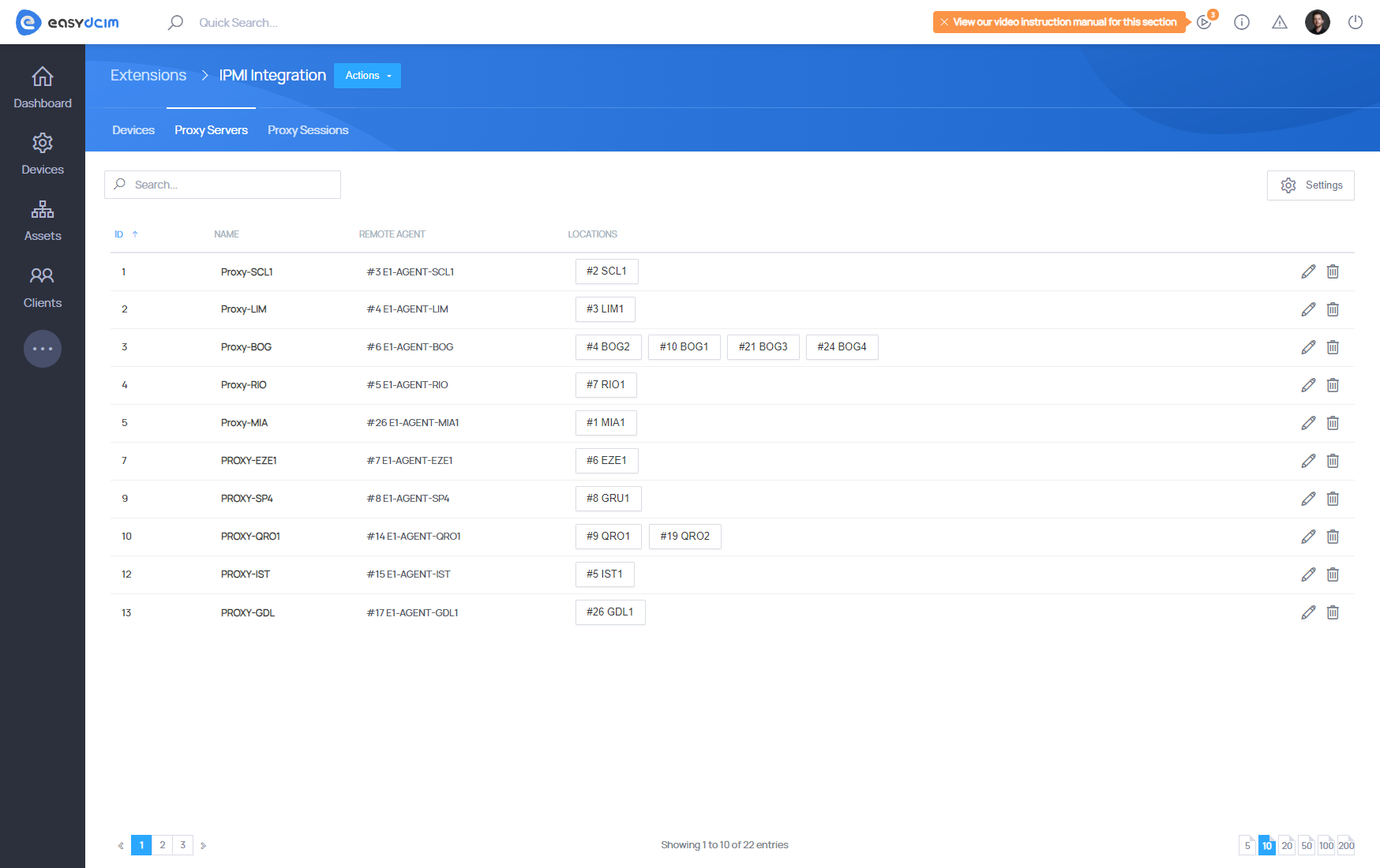
Adding IPMI Proxy Servers
You can add and configure an IPMI proxy server from the IPMI Integration extension. The configuration form for adding an IPMI proxy server contains the following fields:
- Name:: The name of your proxy server.
- Remote Agent:: The remote agent responsible for operating the proxy server.
- Use in Locations:: The locations in which the proxy server will operate. All devices assigned to these locations will be managed through this proxy. You can select one or multiple locations.
- noVNC Proxy Type:: Defines how the proxy server handles KVM or panel redirection. Available options:
- Automatically download and run the JAVA console: Downloads the manufacturer’s Java-based KVM applet and displays it inside a noVNC session.
- Start a web browser with access to the management panel: Opens the factory IPMI web interface and displays it through a noVNC session.
- Start a web browser in debug mode (for local use): Opens the IPMI web interface in debug mode.
- noVNC Java Version:: Specifies the version of Java used by Docker in noVNC sessions.
- Enable Firewall:: Enables the built-in firewall system that restricts access to websites. Activating this option allows you to define firewall rules.
- Disable Login Buttons:: Disables the IPMI Username and IPMI Password buttons inside the noVNC session.
Principle of operation
The remote JAVA console is downloaded directly from the server manufacturer’s panel, using the specific CURL commands. Additionally, to download the JAVA console, you need a public address of the IPMI interface which may lead to unauthorized access. If such a situation occurs, you can create a proxy server for IPMI connections in the application that will serve as a gateway between the application and the end user. The proxy server also channels all IPMI commands such as device power-on, restart or power-off. Owing to such a solution, none of the IPMI interfaces requires a public IP address and all important operations can be carried out in a secure private data center network.
Extension at work
- The VNC server and the software required to display the IPMI interface and the remote console will be installed on the proxy server.
- The webockify server, which redirects traffic to the VNC server and back, will start on the server with EasyDCIM.
- noVNC, which refers to websockify locally and gets an image with the IPMI interface in the browser through the VNC server will be launched on the server with EasyDCIM.
- On the EasyDCIM server, you must allow incoming traffic for the port range from 6081 to 6200.
The following operations are performed on the proxy server:
- Creates a new user called easydcim_vnc_X to be able to start the VNC server
- Installs the necessary system packages (chromium, java etc.)
- Creates an exception file for Java
- Downloading a JAVA console via the remote agent or launching a factory IPMI panel
- Creating a connection between EasyDCIM and the VNC server